Computer hardware is the collection of physical parts of a computer system. This includes the computer case, monitor, keyboard, and mouse. It also includes all the parts inside the computer case, such as the hard disk drive, motherboard, video card, and many others. Computer hardware is what you can physically touch.
A computer system consists of two major elements: hardware and software. Computer hardware is the collection of all the parts you can physically touch. Computer software, on the other hand, is not something you can touch. Software is a set of instructions for a computer to perform specific operations. You need both hardware and software for a computer system to work.
Some hardware components are easy to recognize, such as the computer case, keyboard, and monitor. However, there are many different types of hardware components. In this lesson, you will learn how to recognize the different components and what they do.
Types of Computers
Before looking at the various components, it is useful to distinguish between two different types of computers: desktop computers and laptop computers. A desktop computer consists of a computer case and a separate monitor, keyboard, and mouse. As the name suggests, this type of computer is typically placed on a desk and is not very portable.
A laptop computer has the same components but integrated into a single, portable unit.While these two types of computers look quite different, they have the same general hardware components.
Mainframe computer
A mainframe computer is a much larger computer that typically fills a room and may cost many hundreds or thousands of times as much as a personal computer. They are designed to perform large numbers of calculations for governments and large enterprises.
Departmental Computing
In the 1960s and 1970s, more and more departments started to use cheaper and dedicated systems for specific purposes like process control and laboratory automation.
Supercomputer
A supercomputer is superficially similar to a mainframe, but is instead intended for extremely demanding computational tasks. As of June 2018, the fastest supercomputer on the TOP 500 supercomputer list is the Summit, in the United States, with a LINPACK benchmark score of 122.3 PFLOPS, exceeding the previous record holder, Sunway TaihuLight, by around 29 PFLOPS.
The term supercomputer does not refer to a specific technology. Rather it indicates the fastest computations available at any given time. In mid 2011, the fastest supercomputers boasted speeds exceeding one petaflop, or 1 quadrillion (10^15 or 1,000 trillion) floating point operations per second. Supercomputers are fast but extremely costly, so they are generally used by large organizations to execute computationally demanding tasks involving large data sets. Supercomputers typically run military and scientific applications. Although costly, they are also being used for commercial applications where huge amounts of data must be analyzed. For example, large banks employ supercomputers to calculate the risks and returns of various investment strategies, and healthcare organizations use them to analyze giant databases of patient data to determine optimal treatments for various diseases and problems incurring to the country.
Hardware Components
Basic hardware components of a modern personal computer, including a monitor, a motherboard, a CPU, a RAM, two expansion cards, a power supply, an optical disc drive, a hard disk drive, a keyboard and a mouse. Inside a custom-built computer: power supply at the bottom has its own cooling fan
The personal computer, also known as the PC, is one of the most common types of computer due to its versatility and relatively low price. Laptops are generally very similar, although they may use lower-power or reduced size components, thus lower performance.
Computer Case
The computer case encloses most of the components of the system. It provides mechanical support and protection for internal elements such as the motherboard, disk drives, and power supplies, and controls and directs the flow of cooling air over internal components. The case is also part of the system to control electromagnetic interference radiated by the computer, and protects internal parts from electrostatic discharge. Large tower cases provide extra internal space for multiple disk drives or other peripherals and usually stand on the floor, while desktop cases provide less expansion room. All-in-one style designs include a video display built into the same case. Portable and laptop computers require cases that provide impact protection for the unit. A current development in laptop computers is a detachable keyboard, which allows the system to be configured as a touch-screen tablet. Hobbyists may decorate the cases with colored lights, paint, or other features, in an activity called case modding.
Power supply
A power supply unit (PSU) converts alternating current (AC) electric power to low-voltage DC power for the internal components of the computer. Laptops are capable of running from a built-in battery, normally for a period of hours.
Motherboard
The motherboard is the main component of a computer. It is a board with integrated circuitry that connects the other parts of the computer including the CPU, the RAM, the disk drives (CD, DVD, hard disk, or any others) as well as any peripherals connected via the ports or the expansion slots.
Components directly attached to or to part of the motherboard include:
- The CPU (central processing unit), which performs most of the calculations which enable a computer to function, and is sometimes referred to as the brain of the computer. It is usually cooled by a heatsink and fan, or water-cooling system. Most newer CPUs include an on-die graphics processing unit (GPU). The clock speed of CPUs governs how fast it executes instructions, and is measured in GHz; typical values lie between 1 GHz and 5 GHz. Many modern computers have the option to overclock the CPU which enhances performance at the expense of greater thermal output and thus a need for improved cooling.
- The chipset, which includes the north bridge, mediates communication between the CPU and the other components of the system, including main memory; as well as south bridge, which is connected to the northbridge, and supports auxiliary interfaces and buses; and, finally, a Super I/O chip, connected through the southbridge, which supports the slowest and most legacy components like serial ports, hardware monitoring and fan control.
- Random-access memory (RAM), which stores the code and data that are being actively accessed by the CPU. For example, when a web browser is opened on the computer it takes up memory; this is stored in the RAM until the web browser is closed. RAM usually comes on DIMMs in the sizes 2GB, 4GB, and 8GB, but can be much larger.
- Read-only memory (ROM), which stores the BIOS that runs when the computer is powered on or otherwise begins execution, a process known as Bootstrapping, or "booting" or "booting up". The BIOS (Basic Input Output System) includes boot firmware and power management firmware. Newer motherboards use Unified Extensible Firmware Interface (UEFI) instead of BIOS.
- Buses that connect the CPU to various internal components and to expand cards for graphics and sound.
- The CMOS battery, which powers the memory for date and time in the BIOS chip. This battery is generally a watch battery.
- The video card (also known as the graphics card), which processes computer graphics. More powerful graphics cards are better suited to handle strenuous tasks, such as playing intensive video games.
Expansion cards
An expansion card in computing is a printed circuit board that can be inserted into an expansion slot of a computer motherboard or backplane to add functionality to a computer system via the expansion bus. Expansion cards can be used to obtain or expand on features not offered by the motherboard.
Storage devices
A storage device is any computing hardware and digital media that is used for storing, porting and extracting data files and objects. It can hold and store information both temporarily and permanently, and can be internal or external to a computer, server or any similar computing device. Data storage is a core function and fundamental component of computers.
Fixed media
Data is stored by a computer using a variety of media. Hard disk drives are found in virtually all older computers, due to their high capacity and low cost, but solid-state drives are faster and more power efficient, although currently more expensive than hard drives in terms of dollar per gigabyte, so are often found in personal computers built post-2007.[6] Some systems may use a disk array controller for greater performance or reliability.
Removable media
To transfer data between computers, a USB flash drive or optical disc may be used. Their usefulness depends on being readable by other systems; the majority of machines have an optical disk drive, and virtually all have at least one USB port.
Input and output peripherals
Input and output devices are typically housed externally to the main computer chassis. The following are either standard or very common to many computer systems.
Input
Input devices allow the user to enter information into the system, or control its operation. Most personal computers have a mouse and keyboard, but laptop systems typically use a touchpad instead of a mouse. Other input devices include webcams, microphones, joysticks, and image scanners.
Output device
Output devices display information in a human readable form. Such devices could include printers, speakers, monitors or a Braille embosser.
Below will be the most widely adopted technology trends.Computer Society's predictions based on an in-depth analysis by leading technology experts, identify top technologies that have substantial potential to disrupt the market computer hardware markets. The technical community depends on the Computer Society as the source of technology IP, trends, and information.
The Top 10 technology trends predicted to reach adoption:
 Deep learning accelerators such as GPUs, FPGAs, and more recently TPUs. More companies have been announcing plans to design their own accelerators, which are widely used in data centers. There is also an opportunity to deploy them at the edge, initially for inference and for limited training over time. This also includes accelerators for very low power devices. The development of these technologies will allow machine learning (or smart devices) to be used in many IoT devices and appliances.
Deep learning accelerators such as GPUs, FPGAs, and more recently TPUs. More companies have been announcing plans to design their own accelerators, which are widely used in data centers. There is also an opportunity to deploy them at the edge, initially for inference and for limited training over time. This also includes accelerators for very low power devices. The development of these technologies will allow machine learning (or smart devices) to be used in many IoT devices and appliances.- Assisted transportation. While the vision of fully autonomous, self-driving vehicles might still be a few years away, increasingly automated assistance is taking place in both personal and municipal (dedicated) vehicles. Assisted transportation is already very useful in terms of wide recognition and is paving the way for fully autonomous vehicles. This technology is highly dependent on deep learning accelerators (see #1) for video recognition.
- The Internet of Bodies (IoB). IoT and self-monitoring technologies are moving closer to and even inside the human body. Consumers are comfortable with self-tracking using external devices (such as fitness trackers and smart glasses) and with playing games using augmented reality devices. Digital pills are entering mainstream medicine, and body-attached, implantable, and embedded IoB devices are also beginning to interact with sensors in the environment. These devices yield richer data that enable more interesting and useful applications, but also raise concerns about security, privacy, physical harm, and abuse.
- Social credit algorithms. These algorithms use facial recognition and other advanced biometrics to identify a person and retrieve data about that person from social media and other digital profiles for the purpose of approval or denial of access to consumer products or social services. In our increasingly networked world, the combination of biometrics and blended social data streams can turn a brief observation into a judgment of whether a person is a good or bad risk or worthy of public social sanction. Some countries are reportedly already using social credit algorithms to assess loyalty to the state.
- Advanced (smart) materials and devices. We believe novel and advanced materials and devices for sensors, actuators, and wireless communications, such as tunable glass, smart paper, and ingestible transmitters, will create an explosion of exciting applications in healthcare, packaging, appliances, and more. These technologies will also advance pervasive, ubiquitous, and immersive computing, such as the recent announcement of a cellular phone with a foldable screen. The use of such technologies will have a large impact in the way we perceive IoT devices and will lead to new usage models.
- Active security protection. The traditional method of protecting computer systems involves the deployment of prevention mechanisms, such as anti-virus software. As attackers become more sophisticated, the effectiveness of protection mechanisms decreases as the cost increases. However, a new generation of security mechanisms is emerging that uses an active approach, such as hooks that can be activated when new types of attacks are exposed and machine learning mechanisms to identify sophisticated attacks. Attacking the attacker is a technological possibility as well, but is almost always illegal.
- Virtual reality (VR) and augmented reality (AR). These related technologies have been hitting the mainstream in some respects for a number of years. For a well-known example, Pokemon Go is a game that uses the camera of a smartphone to interpose fictional objects in real-world surroundings. Gaming is clearly a driver of these technologies, with other consumer devices becoming affordable and commonplace. VR and AR technologies are also useful for education, engineering, and other fields. However, there has been a Catch-22 in that there is a lack of applications resulting from the high cost of entry, yet the cost has stayed high due to a lack of applications. With advertisements for VR headsets appearing during prime-time television programs, we may have finally reached a tipping point.
- Chatbots. These artificial intelligence (AI) programs simulate interactive human conversation using key pre-calculated user phrases and auditory or text-based signals. Chatbots have recently started to use self-created sentences in lieu of pre-calculated user phrases, providing better results. Chatbots are frequently used for basic customer service on social networking hubs and are often included in operating systems as intelligent virtual assistants. We have recently witnessed the use of chatbots as personal assistants capable of machine-to-machine communications as well. In fact, chatbots mimic humans so well that some countries are considering requiring chatbots to disclose that they are not human. Industry is looking to expand chatbot applications to interaction with cognitive-impaired children as a way to provide therapeutic support.
- Automated voice spam (robocall) prevention. Spam phone calls are an ongoing problem of increasing sophistication, such as spoofing the caller ID number of the victim's family and business associates. This is leading people to regularly ignore phone calls, creating risks such as true emergency calls going unanswered. However, emerging technology can now block spoofed caller ID and intercept questionable calls so the computer can ask questions of the caller to assess whether he or she is legitimate.
- Technology for humanity (specifically machine learning). We are approaching the point where technology can help resolve societal issues. We predict that large-scale use of machine learning, robots, and drones will help improve agriculture, ease drought, ensure supply of food, and improve health in remote areas. Some of these activities have already started, but we predict an increase in adoption rate and the reporting of success stories in the next year. "Sensors everywhere" and advances in IoT and edge computing are major factors contributing to the adoption of this technology. Recent events, such as major fires and bridge collapses, are further accelerating the urgency to adopt monitoring technologies in fields like forests and smart roads.
Below are some of the technologies we considered very promising but felt that they will reach broad adoption.

- Digital twins. These are software representations of assets and processes to understand, predict, and optimize performance for improved business outcomes. A digital twin can be a digital representation of any characteristic of a real entity, including humans. The choice of which characteristics are digitized is determined by the intended use of the twin. Digital twins are already being used by many companies: according to analysts, 48% of companies in the IoT space have already started adopting them. This includes digital twins for very complex entities, such as an entire smart city (for example, Digital Singapore). Digital twins are also expected to play a transformational role in healthcare over the next three years.
 Real-time ray tracing. RT2 has long been considered the Holy Grail for rendering computer graphics realistically. Although the technique itself is quite mature, it was too compute-intensive to perform in real time until recently—so all ray-traced scenes had to be scripted and rendered in advance. In 2018, we witnessed the debut of a consumer product family with RT2 capabilities. In the next couple of years we expect to see incremental iterations until true RT2 is widespread. Initially, we expect the growth to be driven by consumer applications, such as gaming, followed by professional applications, such as training and simulation. Combined with #7 (VR), this technology could open up new frontiers in high-fidelity visual simulations.
Real-time ray tracing. RT2 has long been considered the Holy Grail for rendering computer graphics realistically. Although the technique itself is quite mature, it was too compute-intensive to perform in real time until recently—so all ray-traced scenes had to be scripted and rendered in advance. In 2018, we witnessed the debut of a consumer product family with RT2 capabilities. In the next couple of years we expect to see incremental iterations until true RT2 is widespread. Initially, we expect the growth to be driven by consumer applications, such as gaming, followed by professional applications, such as training and simulation. Combined with #7 (VR), this technology could open up new frontiers in high-fidelity visual simulations.
- Serverless computing. This is used to refer to the family of lambda-like offerings in the cloud, such as AWS Lambda, Google Cloud Functions, Azure Functions, or Nuclio. "Serverless" is the next step in the continuum along the line of virtualization, containers, and microservices. Unlike IaaS, in serverless computing the service provider manages the resources at a very fine granularity (all the way down to an individual function). End users can focus on the functions and don't have to pre-allocate instances or containers or manage them explicitly. While it's still at an early stage of adoption, there's appeal on both sides (better resource utilization for the providers, and pay-for-what-you-use for the users), so we expect that it will pick up rapidly and we will start seeing significant adoption in the next couple of years.
Finally, we considered some technologies that we felt already reached broad adoption: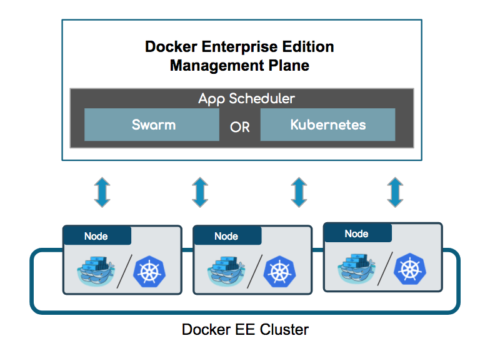
- Kubernetes and Docker. Acceptance of Docker and Google's decision to make Kubernetes open source inspired the wider open source community to stand behind these two technologies. This made Kubernetes one of the most popular open source projects in the last two years and the de facto standard for running containerized distributed applications on on-premises clusters and the public cloud. Kubernetes is already used in production by early adopters, with planned advances in security and reliability expected to attract further use by traditional enterprise companies. In 2019, we expect Kubernetes to be used in lieu of proprietary orchestration infrastructure for running big data processing and refactored open source code.

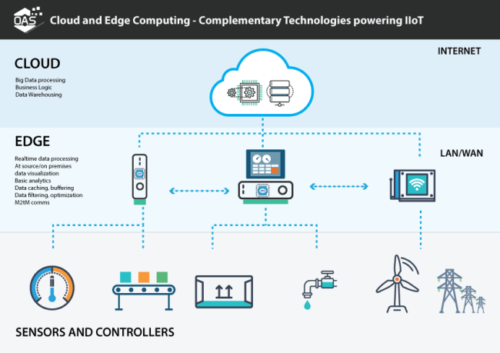
- Edge computing. This is the conversion of IoT data to usable information using microprocessors collocated with the sensor, or at the edge of the network. Edge computing reduces network bandwidth, data storage, and analysis requirements. The price is increased power at the mobile device, requiring innovations in energy harvesting and storage. Innovations in edge computing will accelerate new developments across a wide array of applications.







 Deep learning accelerators such as GPUs, FPGAs, and more recently TPUs. More companies have been announcing plans to design their own accelerators, which are widely used in data centers. There is also an opportunity to deploy them at the edge, initially for inference and for limited training over time. This also includes accelerators for very low power devices. The development of these technologies will allow machine learning (or smart devices) to be used in many IoT devices and appliances.
Deep learning accelerators such as GPUs, FPGAs, and more recently TPUs. More companies have been announcing plans to design their own accelerators, which are widely used in data centers. There is also an opportunity to deploy them at the edge, initially for inference and for limited training over time. This also includes accelerators for very low power devices. The development of these technologies will allow machine learning (or smart devices) to be used in many IoT devices and appliances. Real-time ray tracing. RT2 has long been considered the Holy Grail for rendering computer graphics realistically. Although the technique itself is quite mature, it was too compute-intensive to perform in real time until recently—so all ray-traced scenes had to be scripted and rendered in advance. In 2018, we witnessed the debut of a consumer product family with RT2 capabilities. In the next couple of years we expect to see incremental iterations until true RT2 is widespread. Initially, we expect the growth to be driven by consumer applications, such as gaming, followed by professional applications, such as training and simulation. Combined with #7 (VR), this technology could open up new frontiers in high-fidelity visual simulations.
Real-time ray tracing. RT2 has long been considered the Holy Grail for rendering computer graphics realistically. Although the technique itself is quite mature, it was too compute-intensive to perform in real time until recently—so all ray-traced scenes had to be scripted and rendered in advance. In 2018, we witnessed the debut of a consumer product family with RT2 capabilities. In the next couple of years we expect to see incremental iterations until true RT2 is widespread. Initially, we expect the growth to be driven by consumer applications, such as gaming, followed by professional applications, such as training and simulation. Combined with #7 (VR), this technology could open up new frontiers in high-fidelity visual simulations.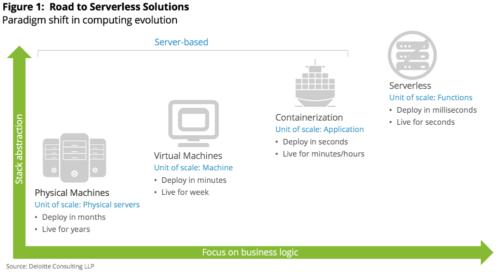












Leave a Reply to simon Cancel reply