Biometry" in literal terms means "measurement of life". In a broader sense, it designates the quantitative study of living beings. It covers a wide range of applications, including anthropology and medicine.
The Term "Biometrics" is the measurement and statistical analysis of people's unique physical and behavioral characteristics. The technology is mainly used for identification and access control, or for identifying individuals who are under surveillance. The basic premise of biometric authentication is that every person can be accurately identified by his or her intrinsic physical or behavioral traits.
Biometrics - Applications in Real World
History of Biometrics:
An early cataloging of fingerprints dates back to 1891 when Juan Vucetich started a collection of fingerprints of criminals in Argentina. Josh Ellenbogen and Nitzan Lebovic argued that Biometrics is originated in the identificatory systems of criminal activity developed by Alphonse Bertillon (1853–1914) and developed by Francis Galton's theory of fingerprints and physiognomy. According to Lebovic, Galton's work "led to the application of mathematical models to fingerprints, phrenology, and facial characteristics", as part of "absolute identification" and "a key to both inclusion and exclusion" of populations. Accordingly, "the biometric system is the absolute political weapon of our era" and a form of "soft control". The theoretician David Lyon showed that during the past two decades biometric systems have penetrated the civilian market, and blurred the lines between governmental forms of control and private corporate control. Kelly A. Gates identified 9/11 as the turning point for the cultural language of our present: "in the language of cultural studies, the aftermath of 9/11 was a moment of articulation, where objects or events that have no necessary connection come together and a new discourse formation is established: automated facial recognition as a homeland security technology."
How biometrics work
Authentication by biometric verification is becoming increasingly common in corporate and public security systems, consumer electronics, and point-of-sale applications. In addition to security, the driving force behind biometric verification has been convenience, as there are no passwords to remember or security tokens to carry. Some biometric methods, such as measuring a person's gait, can operate with no direct contact with the person being authenticated.
Types of biometrics
The two main types of biometric identifiers depend on either physiological characteristics or behavioral characteristics.
Physiological identifiers relate to the composition of the user being authenticated and include facial recognition, fingerprints, finger geometry (the size and position of fingers), iris recognition, vein recognition, retina scanning, voice recognition and DNA matching.
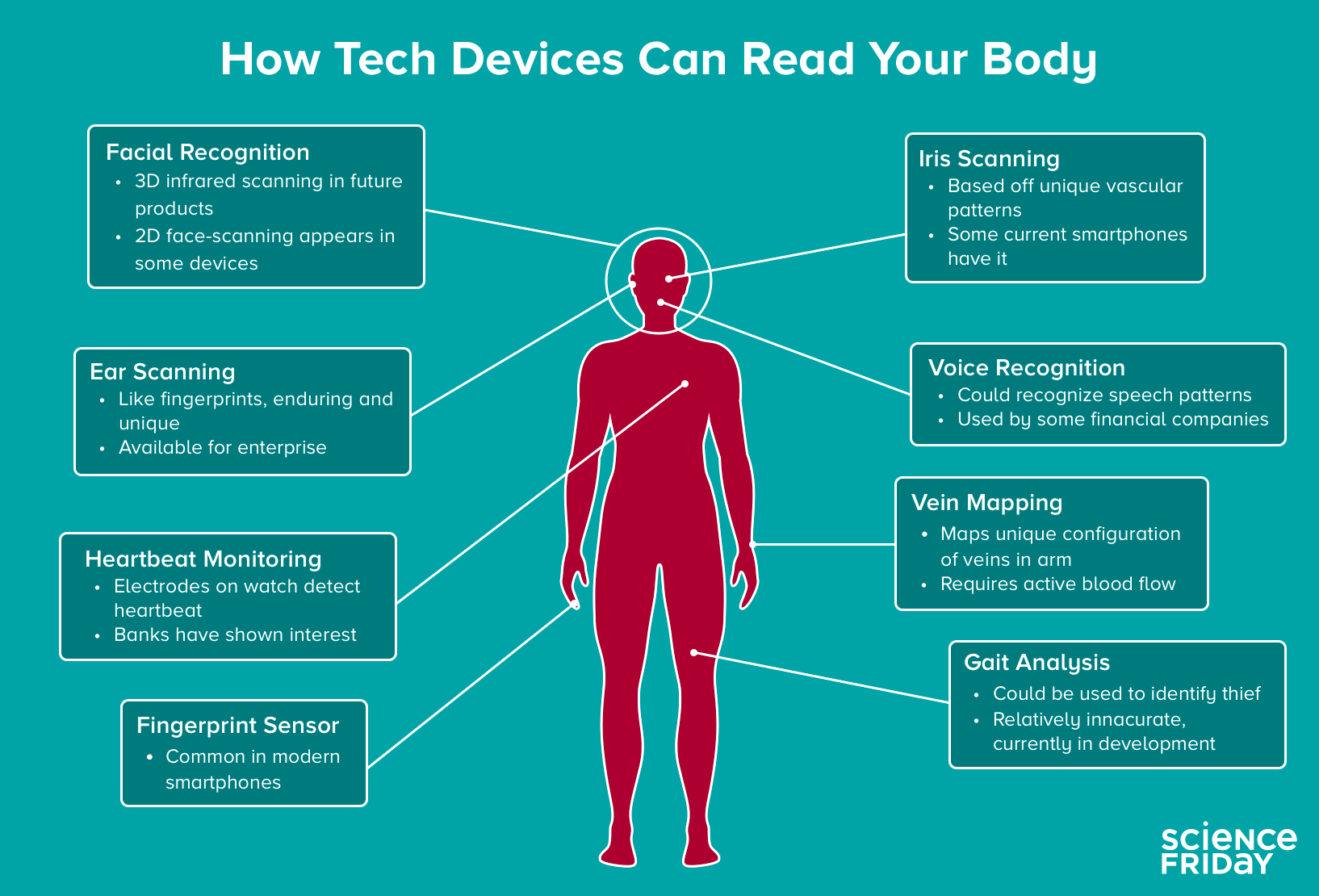
Behavioral identifiers include the unique ways in which individuals act, including recognition of typing patterns, walking gait and other gestures. Some of these behavioral identifiers can be used to provide continuous authentication instead of a single one-off authentication check.
Components of biometric devices include:
- A reader or scanning device to record the biometric factor being authenticated
- Software to convert the scanned biometric data into a standardized digital format and to compare match points of the observed data with stored data
- A database to securely store biometric data for comparison
Biometric data may be held in a centralized database, although modern biometric implementations often depend instead on gathering biometric data locally and then cryptographically hashing it, so that authentication or identification can be accomplished without direct access to the biometric data itself.
Applications of Biometrics
BIOMETRICS AND CIVIL IDENTITY - Establishing and protecting a person's unique identity
One of a State's main missions is to guarantee the identity of its citizens. Digital transformation of society and economies are driving countries to meet new challenges to protect their citizens against identity theft and provide safe, online services. Biometrics helps address this challenge: it links our identities with our physical and digital selves. This reduces the risk of identity theft, and facilitates the implementation of new identity management services which are both practical and secure. Morpho supports governments at several levels:
- Taking censuses of populations and creating civil identity registries: biometric registration of citizens and data management.
- Issuance of secure ID documents:national e-ID cards, biometric passports, e-driver's licenses, etc.
BIOMETRICS AND DIGITAL SECURITY - Guaranteeing people's identities and making online transactions safe
Biometrics, whether used on a PC, smartphone or tablet, is a viable alternative to passwords and other identifiers. It guarantees people's identities to ensure the security of online operations and services:- Secure transactions
- Secure payments: biometric bank cards, payment by selfie check or by fingerprint recognition, etc.
- Online authentication: filing tax statements, etc.
- Secure healthcare services: reliable patient identification and identity monitoring.
BIOMETRICS AND PUBLIC SECURITY - Investigations and ensuring the security of public areas and critical infrastructures
Biometrics facilitates investigations by law enforcement units. The biometric systems from are deployed in over 70 countries, by different security agencies. Biometric technologies are also used at borders: they can detect suspicious persons, or authorize access for persons who do not entail a risk.
- Support for law enforcement: multi-biometric identification systems, including video analysis, ID checks, etc.
- Passenger facilitation in airports:reliable identification at borders, automated or accelerated control processes, etc.
- Secure access to public areas or critical infrastructures: biometric gates with facial recognition, access control gates based on fingerprint recognition, etc.
Biometrics - Usage and Benefits
Security and privacy issues of biometrics
Biometric identifiers depend on the uniqueness of the factor being considered. For example, fingerprints are generally considered to be highly unique to each person. Fingerprint recognition, especially as implemented in Apple's Touch ID for the iPhone, is the first widely used mass market application of a biometric authentication factor. Other biometric factors, including retina, iris, vein, voice and facial scans, have not been adopted widely so far, in some part because there is less confidence in the uniqueness of the identifiers or because the factors are easier to spoof.
Stability of the biometric factor can also be important to acceptance of the factor. Fingerprints do not change over a lifetime, while facial appearance can change drastically with age, illness or other factors. The greatest privacy issue of using biometrics is that physical attributes like fingerprints and retinal blood vessel patterns are generally static and cannot be modified. This is in distinction to non-biometric factors like passwords (something you know) and tokens (something you have), which can be replaced if they are breached or otherwise compromised, including over 20 million individuals whose fingerprints were compromised in the 2014 U.S. Office of Personnel Management data breach.
The increasing ubiquity of high-quality cameras, microphones and fingerprint readers in many of today's mobile devices means biometrics will continue to become a more common method for authenticating users, particularly as Fast ID Online (FIDO) has specified new standards for authentication with biometrics that support two-factor authentication with biometric factors.
While the quality of biometric readers continues to improve, they can still produce false negatives -- when an authorized user is not recognized or authenticated -- and false positives -- when an unauthorized user is recognized and authenticated.
Vulnerabilities
While high-quality cameras and other sensors help enable the use of biometrics, they can also enable attackers. Because people do not shield their faces, ears, hands, voice or gait, attacks are possible simply by capturing biometric data from people without their consent or knowledge.
Other biometrics factors can also be defeated by determined attackers.
In 2015, Jan Krissler, also known as "Starbug," a Chaos Computer Club biometrics researcher, demonstrated a method for extracting enough data from a high-resolution photograph to defeat iris scanning authentication; in 2017, Krissler reported defeating the iris scanner authentication scheme used by the Samsung Galaxy S8 smartphone. Krissler had previously recreated a user's thumbprint from a high-resolution image to demonstrate that Apple's Touch ID fingerprinting authentication scheme was also vulnerable.
After Apple released the iPhone X, it took researchers just two weeks to bypass Apple's Face ID facial recognition using a 3D-printed mask; Face ID can also be defeated by individuals related to the authenticated user, including children or siblings.
Future Trends in Biometrics
The market share of biometric technology in today's business is skyrocketing, it is predicted to exceed approximately 32.73 Billion USD by 2022.
Biometrics have changed the traditional security systems around the world. Developed nations like US, UK, Australia, Canada, Japan, China, etc. have already adopted biometrics technologies in the major airports. Major private corporations started using these technologies for workforce management which help them to reduce payroll error, buddy punching, etc.
As per research findings, some biometric technologies which are going to rule in 2018 are the following:
Gait Biometrics:
One of the most advanced biometrics technologies to be available in 2018. If you watched the movie Mission Impossible 5, you already know how it works. In short, it scans the way people walk and move. As everyone has a unique style of walking and moving, it is quite the perfect technology which will rule the future of biometrics from 2018.
Heartbeat Measurement:
It is one of the most critical biometric technologies so far. The growing evolution of biometrics has already replaced the demand for passwords and PINs. But heartbeat biometrics will replace the necessity of car keys, house keys, credit cards, and boarding passes too. Heartbeat is also a unique human characteristic, as like fingerprint, retina, palm veins, etc. It seems like this technology will allow you to sit in front of your laptop and unlock automatically, and when you go for a walk, it’ll be locked again so that nobody can login to your pc. The same thing will happen with your car wheel, door handle, etc.
Keystrokes Dynamics:
Keystroke dynamics (also known as typing biometrics) will scan the pattern of your keystrokes. It is also a behavioral biometric as like heartbeat biometrics. In this method, the biometric device will identify you by your typing pattern, rhythm and speed. Mostly, keystroke recognition will work on computer keyboards, mobile phones, and touchscreen panels. It is very useful for corporations because you need nothing but a keyboard to verify yourself. It is also a unique human characteristic which is difficult to recreate.
Sweat Recognition:
It is a new and unique addition to biometric authentication when you just need to verify yourself with your sweat. Your physical traits such as fingerprint, retina, palm vein can be copied, but your sweat is one of a kind and hard to forge by anyone. The best part of this technology is everybody, including the people without eye or finger or unable to memorize things, can be recognized by the sweat recognition
Odor Recognition:
Your body odor could also be your identity card in the upcoming future of biometrics. A report says that researchers at Spain’s Universidad Politecnica de Madrid and tech firm IIia Sistemas SL are developing a system that can verify people by their scent signatures. Other biometric authentication systems, such as facial recognition, have higher error rates which is highly concerning for researchers. As body odor is unique and everybody can be enrolled by this technology much like sweat recognition, it is deemed more reliable and widely applicable.
About the Author
The author is a well known risk management Professional with an exposure Global Security, Information Management, Criminal and Investigative Research.[1] Biometrics Definition - https://searchsecurity.techtarget.com/definition/biometrics [2] Future Technologies in Biometrics - https://biometrictoday.com/5-technologies-future-biometrics-authentication/ [3] History of Biometrics - https://en.wikipedia.org/wiki/Biometrics








Leave a Reply